Assessing danger
Find out more about the characteristics you can use to recognise fraudulent e-mails, how to deal with such e-mails correctly and where you can get help if you need it.
Characteristics of fraudulent e-mails
Please only open attachments and links in e-mails after taking a critical look. The following characteristics should make you suspicious:
Implausible receipt
Is the receipt of the e-mail plausible? If you placed an order a few minutes ago, it makes sense that you got a confirmation of your order by e-mail.
Request is urgent
The e-mail conveys urgency. In fraudulent e-mails, you are often urged to act quickly. Take the time to scrutinise the e-mail thoroughly before taking any action.
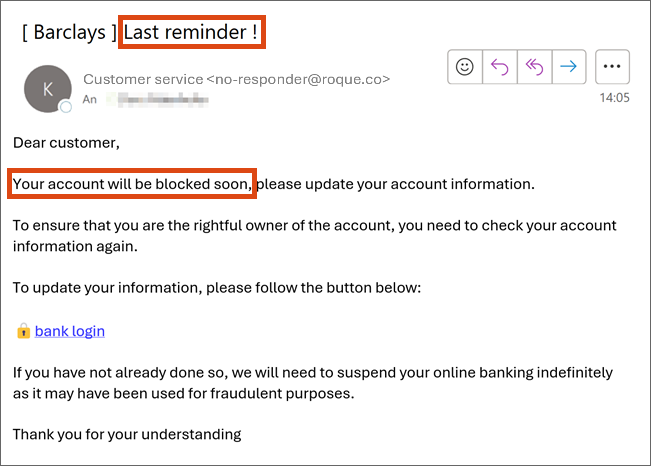
Sender’s e-mail address implausible
Check whether the e-mail address corresponds to the name of the sender and if it is plausible. It is possible to forge a sender address. However, most scammers do not bother doing so.
If the e-mail address is not displayed:
- On the PC: Move the mouse cursor over the sender name without clicking on it. A window with the address will then open.
- On a smartphone or tablet: Tip on the sender’s name or the sender’s icon.
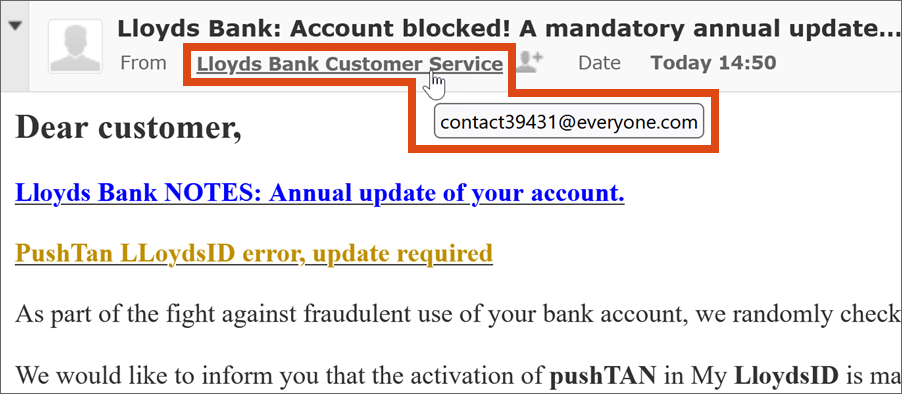
Checking sender’s address
No e-mail attachment requested
You receive an e-mail with an attachment, but have not explicitly requested it. Malware is often hidden in attachments. Therefore, be cautious if you receive an attachment that you did not request.
Stylistically suspicious
If a personal form of address is missing, the text contains many spelling and grammatical errors and umlauts or special characters are not displayed correctly, this might indicate a fraudulent e-mail.
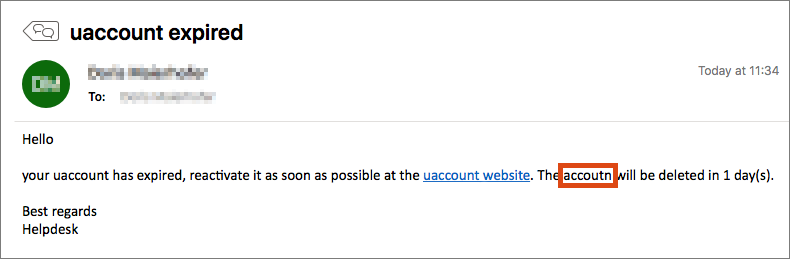
Money transfer or voucher cards requested
Be particularly careful if the e-mail contains a request to transfer money or buy gift cards (e.g. for the Google Play Store or Amazon). Do not comply with such a request. More information: Knowing dangers in e-mails – fraud
Switch to another communication channel requested
The sender wants to switch to a different communication channel, such as a messenger service. Changing the channel allows the attacker to bypass the spam filter of the University of Vienna.
Target address of links or buttons implausible
To check the target address of links or buttons:
- On the PC: Move your cursor over the link in the e-mail without clicking it.
- On a smartphone or tablet: Press the link and hold it down. A window will open with the target address.
Check whether the link would open a website that corresponds to the sender or the context of the e-mail.
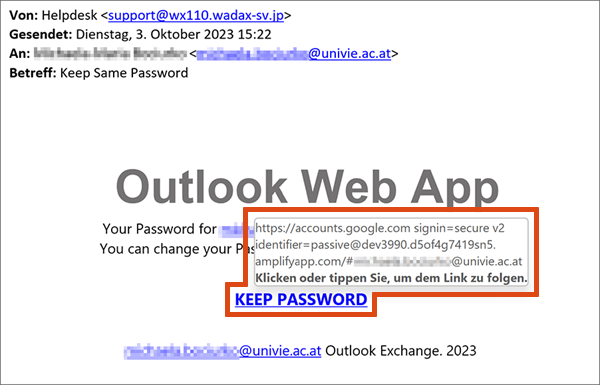
Checking target address of links
In case of uncertainty
If you are still unsure whether the message is authentic,
- obtain information about currently circulating forgeries, for example on the website Watchlist Internet (in German) or use the corresponding smartphone app for iOS or Android free of charge. Even if you cannot find the message on Watchlist Internet, it could still be a forgery.
- contact the sender using another communication channel, for example by telephone. Do not trust the contact information stated in the e-mail, but instead research them yourself.
- contact your IT representative, the ZID Helpdesk, the ZID IT security team or other qualified persons of trust.
Dealing with a fraudulent e-mail
If you suspect or are certain that the message you received is a fraudulent e-mail,
- do not open any attachments that the e-mail may contain.
- do not click any links in the e-mail.
- do not reply to this e-mail.
- do not forward the e-mail except to the ZID IT security team (security.zid@univie.ac.at) or to other qualified experts for analysis purposes. In this case, make sure to send the e-mail as an attachment in the form of an EML file. This allows for analysing the metadata of the e-mail. Follow the steps in the user guide Forwarding e-mails as an attachment.
