Knowing dangers in e-mails
Fraudulent e-mails usually have one of the following 3 objectives: Intercepting access data (phishing), smuggling malware onto a device or committing financial fraud. You can find out more about these dangers on this page.
Phishing
Understanding phishing
Phishing means that unauthorised persons obtain personal login data (user name and password). In phishing e-mails, users are asked to log in to linked websites and online forms. These look like legitimate websites or forms.
Therefore, enter your u:account UserID and password only on websites
- whose address starts with
https://or where the lock symbol is displayed and - whose address contains
….univie.ac.at/.
If there is nothing after this, the final slash is also omitted.
Recognising the target address of a linked web page
Background: Schloss zu, alles gut? (Lock closed, all good?, in German)
Note
If you have mistakenly entered your u:account login data on a third-party or a presumably fraudulent website, or if your computer has been infected by malware, change your u:account password immediately. In case of questions or uncertainties, please contact the IT security team via the Servicedesk.
Examples
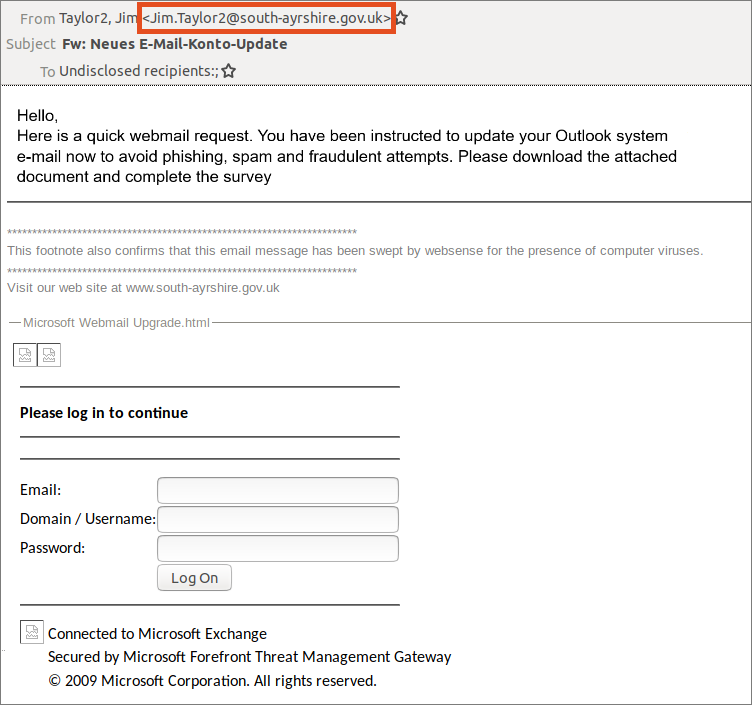
The following e-mail tries to make you believe that you need to update your e-mail account using the form sent with it. You can recognise the fraudulent intent from the sender’s e-mail address.
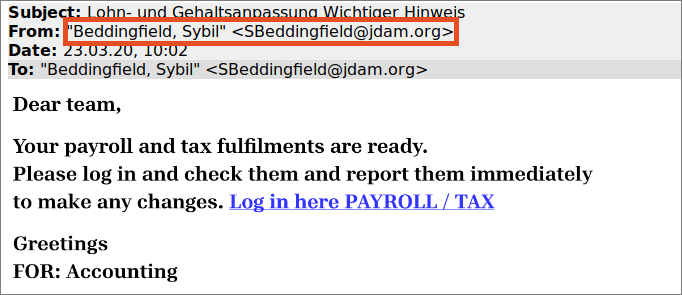
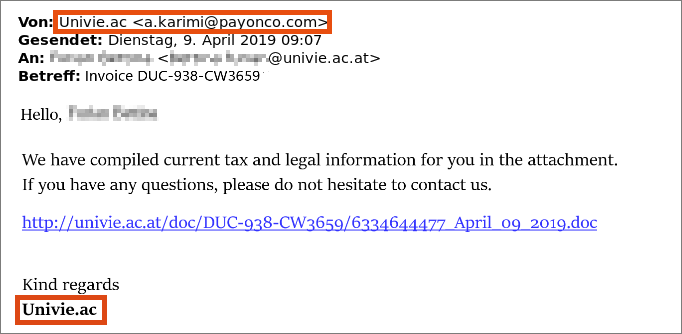
Fraudsters also send links to fake registration forms that you can use to retrieve an alleged payslip or an important document, as the screenshot below shows. Here too, the sender address makes the fraudulent intention clear.
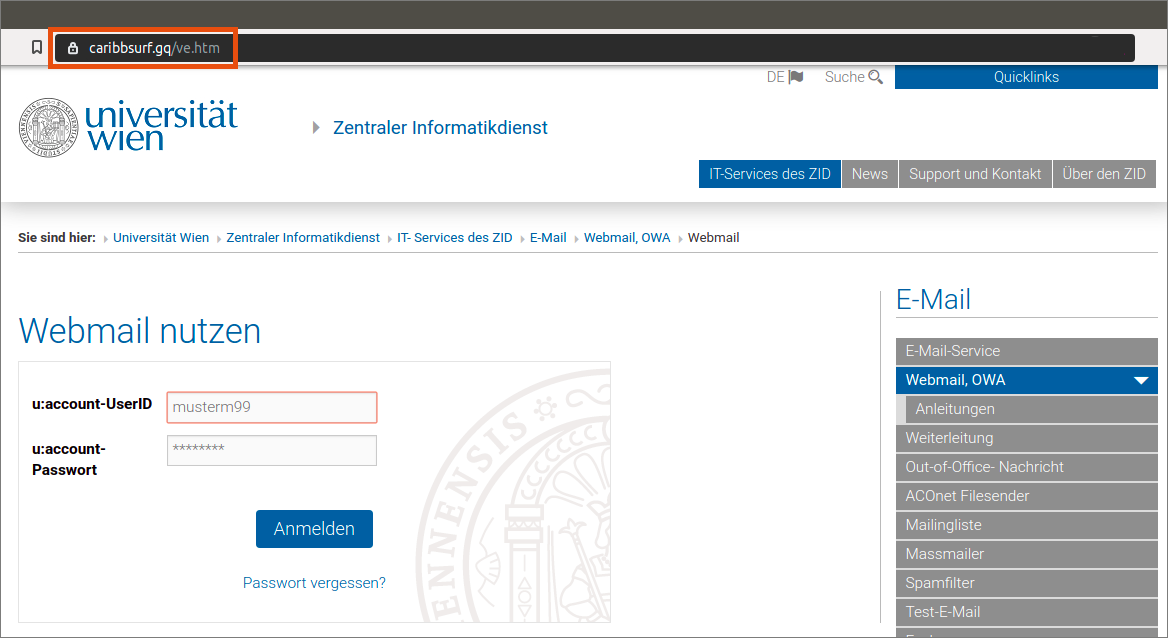
This website looks like the login form of the Webmail service of the University of Vienna. You can recognise that it is a phishing website by looking at the URL in the address bar of the browser.
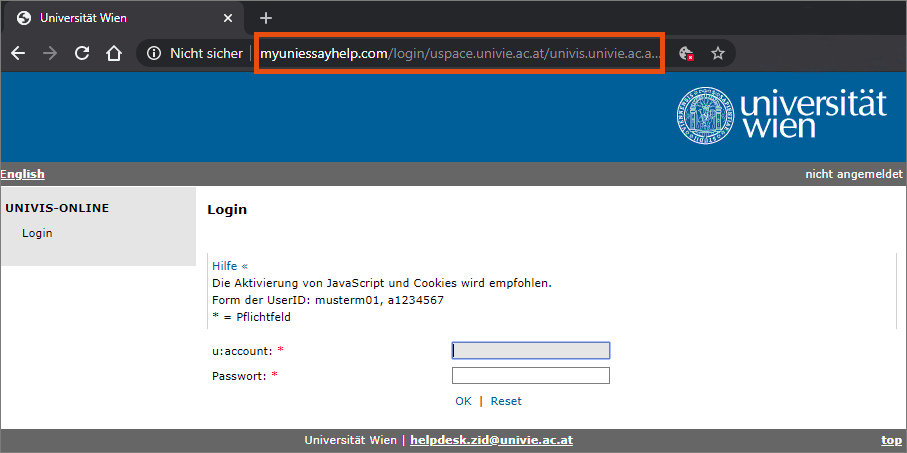
This screenshot shows a fake login form for UNIVIS-Online. The URL in the address bar shows that this form is a fraudulent website.
Malware
Understanding malware
Malware are types of software that enable attackers to access other people’s devices. The aim is to encrypt data via ransomware, transfer data to unauthorised persons or cause damage otherwise. Attackers can also steal your login data that you use for various internet services (such as u:account, online shops, online banking).
Malware can be hidden in attachments and links in e-mails, usually in Word or Excel documents or in compressed files (ZIP). These ZIP files can also be encoded with a password. As soon as they are unzipped using the password, the malware they contain can become active on your device.
You can take the following technical steps against malware:
- Regularly update the operating system (Windows, macOS, iOS, Android) and the software (Outlook, Thunderbird, etc.) that you use. More information: PC and laptop in daily use.
- Keep the virus scanner you use up to date and pay attention to any notifications from your system about the virus scanner.
Example
The following screenshot shows an e-mail requesting the download of a document. This document contains malware.
You need to be particularly careful when
- you do not know the sender and the e-mail address
- the subject line sounds very generic
- you have not requested a documents
Fraud
In addition to stealing (access) data, attackers can also aim to steal money. Such e-mails are often particularly difficult to detect as they are tailored to their addressees.
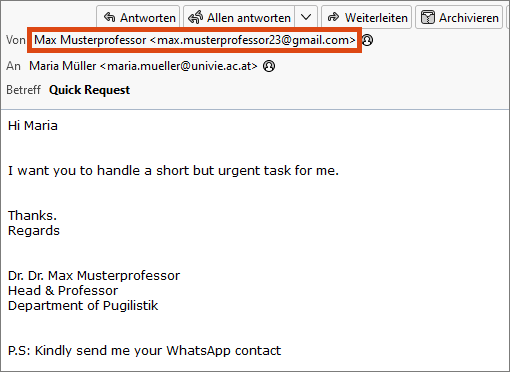
Members of the University of Vienna repeatedly receive e-mails with sender names that resemble those of professors and heads of departments and divisions of the University. The personal form of address is correct and the content is usually a question about whether the recipient is available or willing to help. In further e-mails, recipients are usually asked to transfer money or to purchase and transfer credit, for example in the form of prepaid cards.
In such cases, make sure to pay attention to the sender’s e-mail address. Often, it is easy to clearly identify it as a fake. However, there are also examples where the address seems plausible at first glance, as the following screenshot shows:
Do not reply to these e-mails and never follow instructions to transfer money or credit.
If you are unsure whether it is a fake e-mail, ask via another, official communication channel. Use the contact details of the person in u:find, such as the u:phone or business phone number or the university e-mail address (example: max.muster@univie.ac.at).
